Establishing and Verifying Identity in a modern and more connected world
In the expansion of our digital world, the management of identities has become a critical concern. Personally, for individuals, and more holistically for organizations in many sectors, including finance, healthcare, e-commerce, and government.
The proliferation of online services and the constant threat of cyberattacks and identity theft have underscored the importance of robust identity verification systems.
Digital Transformation and Identity Management
A more digital society has brought numerous conveniences, enabling the individual, to access services, conduct transactions, and communicate seamlessly across the globe. This digital evolution has also given rise to new challenges, primarily in the realm of identity management and verification.
The many online services have created a demand for efficient and secure identity verification systems. People now perform a myriad of activities online, from shopping and banking to social networking and e-health consultation.
As more personal information is stored online, bad actors and cybercriminals have increasingly targeted individuals’ identities for malicious purposes. Identity theft and fraud pose significant threats to both the individual and the many organizations that they potentially engage with.
Governments and regulatory bodies have recognized the importance of safeguarding personal information. Regulations like the General Data Protection Regulation (GDPR) and Know Your Customer (KYC) requirements in the financial and health sector emphasize the need for robust identity verification.
Users expect seamless and user-friendly experiences when interacting with online services and the cumbersome identity verification processes and systems of yesteryear can lead to user frustration and disengagement.
The rise of digital identity and IVS
Identity verification systems (IVS) have emerged as a vital component of modern digital ecosystems. They play a pivotal role in confirming the identity of individuals, enabling secure access to online services, and mitigating the risk of identity-related fraud.
IVS plays a crucial role in various sectors, including finance, healthcare, e-commerce, and government, to ensure that users are who they claim to be, enhance security, and comply with regulatory requirements.
For the public, organizations that rely on establishing a strong identity verification process foster increased trust between the user and the service providers. Users are more likely to engage with services they trust, leading to increased customer retention and loyalty.
Efficiency in the identity verification process also streamlines onboarding processes and reduces the need for manual verification, lowering operational costs for organizations.
Verified identities also provide improved opportunities for personalized experiences and recommendations, enhancing user engagement and satisfaction.
E-government (short for electronic government) is the use of technological communications devices, such as computers and the Internet, to provide public services to citizens and other persons in a country or region. E-government offers new opportunities for more direct and convenient citizen access to government and for government provision of services directly to citizens. Effective E-government is more easily achieved through the establishment of IVS.
His Majesty’s Revenue and Customs (HMRC) is the tax authority in the United Kingdom. HMRC uses a digital identity verification system to ensure secure access to its online services. Similarly, the US IRS (Internal Revenue Service) is the tax authority in the United States. It has implemented various digital identity verification systems to protect taxpayers’ information and prevent fraud.
Singpass is Singapore’s national digital identity system. It provides residents with a trusted digital identity for secure transactions with over 2,700 services offered by more than 800 government agencies and businesses. The Singpass National Digital Identity (NDI) scheme allows residents to seamlessly access government services and third-party apps, such as banks, colleges, professional bodies, and insurance companies.
Estonia has built one of the world’s leading e-governments with a robust digital identity verification system. Estonia’s digital public infrastructure delivers automated and reusable government services in a human-centric, secure, and private way. The country has made its building blocks open-source, available as global digital public goods for others to use. Estonia’s digital services have played a crucial role during the COVID-19 pandemic, enabling citizens to access services online without the need for physical presence
ID.me offers a US-based identity proofing and group affiliation verification that also meets the federal standards for consumer authentication. NIST 800-63-3 IAL2 and AAL2 conformant and EPCS standards, amongst others.
ID.me’s digital wallet and identity verification service simplifies how over 112M individuals discover and access benefits and services through a single login and verified identity from over 600 partners. It provides users with a trusted digital ID card to access government services and benefits. or example, you can use your verified digital ID card to manage your IRS online account, access Social Security Administration benefits and services, manage unemployment benefits and services from various state departments of labor. ID.me also offers discounts and cashback from over 5,000 stores. ID.me also provides an Rx Card that can help you save up to $95 per prescription at participating pharmacies.
ID.me’s simplicity is that it reaches out to consumers to promote the simplicity of proving their identity online, as well as helping businesses provide marketing promotions and bonuses to verified eligible users. Under the hood, it checks to see whether the customer belongs to an eligible group and triggers an invitation to the promotion. The ID.me mission statement stresses “No Identity Left Behind” promising to enable this functionality to everyone, regardless of background or banked status.
Identity Verification Approaches
The establishment and verification of identity are multifaceted processes that require careful consideration of various factors. Several approaches and technologies are employed to verify identities effectively.
In some instances the eGovernment services provide a means of identity verification that a business can leverage however these services may not be available or authorized for commercial use.
Biometrics for identity verification uses physiological characteristics to identify individuals. Biometric features may include facial recognition, fingerprints, iris or retina scans, voice recognition, hand geometry, or even behavioral traits such as typing patterns or walking gait. Such features are captured by sensors and compared with pre-existing biometric data stored in a database to confirm or deny the identity of the person. Biometric authentication systems are increasingly popular in areas such as banking, security, and mobile devices since they are considered to be more secure than traditional methods of identification, such as passwords or personal identification numbers (PINs), they are much harder to forge or steal.
Document scanning of ID documents such as passports or driver’s licenses for identity verification is a common practice in various contexts. Organizations and agencies may use ID scanning to take electronic copies of documents that prove your identity, such as driver’s licenses. ID scanning can help verify the authenticity of government-issued identifications and streamline identity verification processes.
Knowledge-Based Authentication (KBA) is an authentication method that verifies user identity by asking specific security questions. When setting up a new account, users are often required to create a password and choose security questions and answers, such as “What is your mother’s maiden name?”. During login or other actions, users are prompted to answer these security questions based on personal information. KBA can be categorized into two types: Static Knowledge-Based Authentication (SKBA) and Dynamic Knowledge-Based Authentication (DKBA).
Static Knowledge-Based Authentication requires users to provide answers to one or more security questions during account creation. The answers can be accurate or made up, as long as the user remembers them when prompted later. Enterprises need to be cautious when selecting the type and number of questions to avoid being intrusive or excessive.
Dynamic Knowledge-Based Authentication (DKBA) provides a higher level of security but is used less frequently. It relies on information collected from different data sources to generate real-time questions. For example, a user may be asked, “Which of the following companies did you not work for?” and presented with a list of former employers and one incorrect answer.
While KBA is still widely used, it has certain limitations. Personal information used for KBA can often be discovered or stolen through research, phishing, social engineering, or data breaches. People also freely share the same information on social media sites, reducing its security value. Passwords can be shared, stolen, or cracked using password-cracking tools. To enhance security, enterprises relying on KBA should reinforce it with more secure methods like MFA (Multi-Factor Authentication).
SMS or Email Codes are increasingly popular for identity verification, wherein users receive a one-time code via SMS or email, which they must enter to complete the verification process. These are extensions to older, but still popular methods like tokens; where physical devices or mobile device software generates time-based or event-based codes for authentication.
Contemporary blockchain technology offers a decentralized and tamper-resistant approach to identity verification, allowing users to control their identity data securely.
Challenges in Identity Verification
Biometric data, such as fingerprints or facial scans, is highly personal and sensitive. If not adequately protected, it can be vulnerable to data breaches or unauthorized access. Further, storing biometric data in centralized databases can create a single point of failure and increase the risk of identity theft or misuse.
Organizations must comply with local, regional, and national data protection regulations when collecting, storing, and processing biometric and other personal data. There needs to be proper consent, secure storage, and appropriate retention periods for identity and other personally identifiable information.
Biometric systems may have false acceptance or false rejection rates, leading to incorrect identification or denial of access. Factors such as changes in physical appearance, injuries, or aging can affect the accuracy of biometric matching. Denial of service or access can prove challenging under such circumstances. Compromised credentials and stolen devices present the same risks. Some of these approaches may also not work equally well for everyone. Factors such as skin color, gender, age, or disabilities can impact the accuracy and inclusivity of biometric identification systems, for example. Biases in training data or algorithms can also result in discriminatory outcomes.
Ultimately, users should have control over their biometric and other data and be able to provide informed consent for its collection and use. Organizations should be transparent about how individuals’ data is used and allow them to opt-out if desired.
IVS Market offerings
Identity verification systems have risen to prominence due to the digital transformation and the growing importance of securing personal information in the digital age. These systems provide enhanced security, regulatory compliance, improved user trust, and operational efficiencies. Various approaches, including biometric authentication, document verification, and blockchain-based solutions, are employed to establish and verify identity.
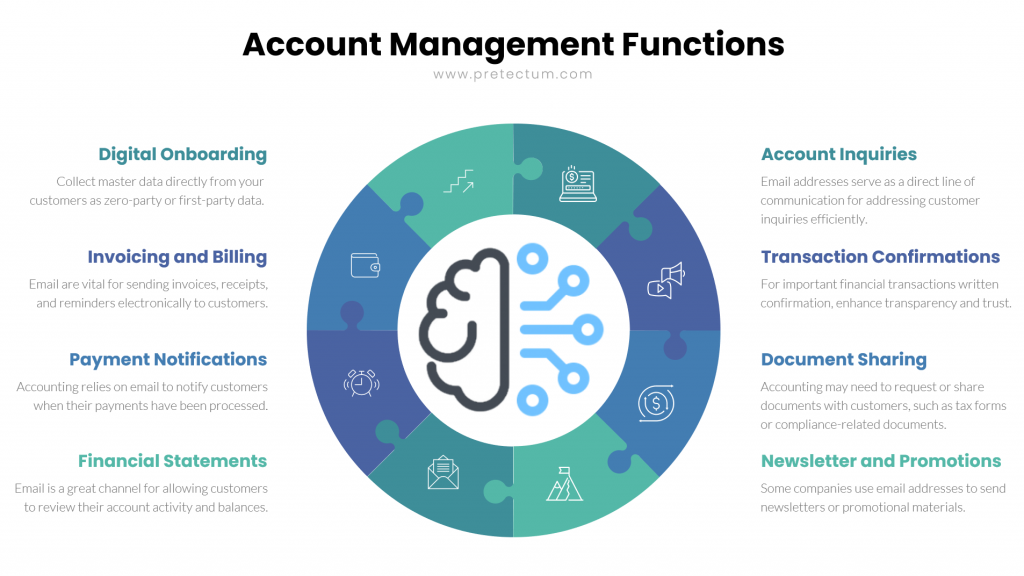
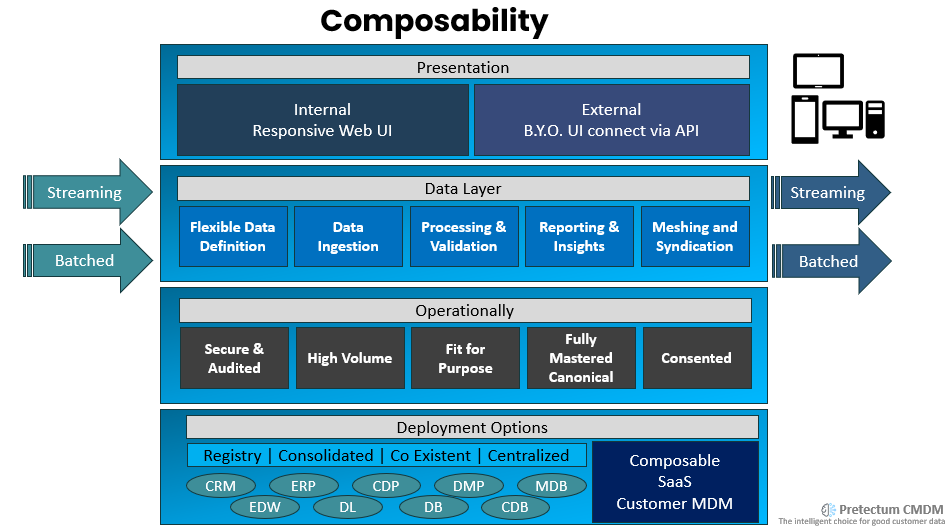
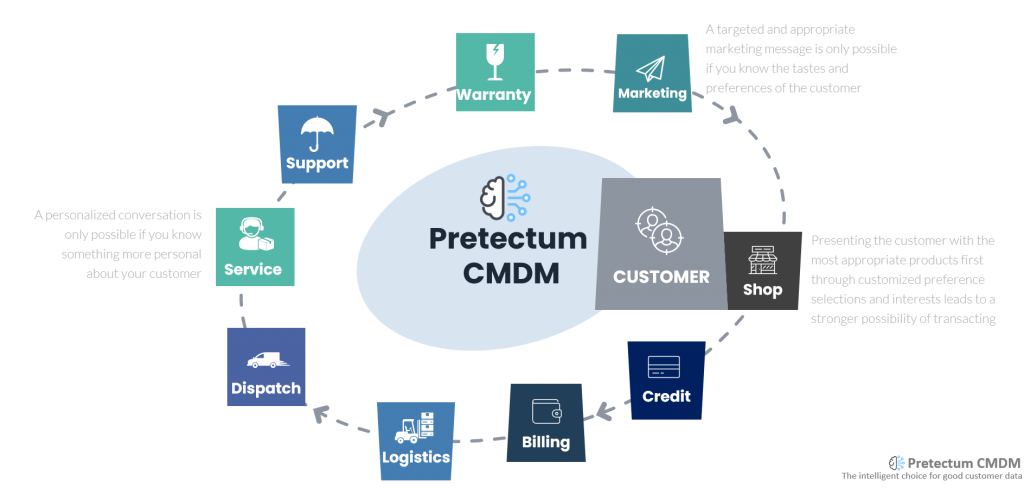
Customer Master Data Management (CMDM) primarily revolves around managing and maintaining customer data within the organization. Its core purpose is to create a unified and accurate view of customer information, ensuring consistency and reliability across various systems and departments. The Pretectum CMDM achieves this through data integration, quality management, governance practices, and consolidation efforts. Its use cases span a wide spectrum, from improving customer relationship management to enhancing data analytics and supporting marketing campaigns, sales, and customer service. Customer MDM aggregates customer data from diverse sources within your organization, amongst them, CRM, ERP. CDP, marketing and sales systems, and databases.
In contrast, IVS is tailored specifically for the critical task of verifying the identity of individuals accessing online services or systems. Its primary objective is to confirm that the person claiming to be a customer is indeed who they claim to be. IVS accomplishes this through a range of methods. IVS finds applications in online services, financial institutions, government agencies, and any organization that requires secure user authentication. Its role is to prevent fraud, secure access to sensitive data, and adhere to regulatory mandates such as Know Your Customer (KYC) requirements. IVS primarily relies on data provided by users during the verification process, including biometric data, scanned identification documents, or responses to security questions.
When comparing CMDM and IVS, several distinctions and intersections emerge. CMDM is more encompassing in scope, addressing all facets of customer data management, including data quality, integration, and governance. IVS, conversely, maintains a narrower focus on identity verification. Both CMDM and IVS contribute to regulatory compliance, with CMDM ensuring data accuracy and consistency, which is vital for adhering to data protection regulations, while IVS plays a pivotal role in identity verification and KYC compliance.
In essence, CMDM and IVS are complementary elements in the digital ecosystem. CMDM like the Pretectum Customer MDM aids in maintaining data accuracy and providing a holistic view of customer data for internal purposes within an organization, while IVS specializes in the crucial task of verifying the identity of users for the sake of security and controlled access. Both are indispensable for ensuring data accuracy, safeguarding digital interactions, and aligning with regulatory requirements. While their scopes and functions differ, they work in tandem to support trustworthy and efficient digital operations in an increasingly connected world.
Organizations must navigate the many challenges related to privacy, user experience, false positives/negatives, scalability, regulatory compliance, and continuous monitoring by appropriately selecting technologies and practices aligned with their specific operational needs.
By adopting appropriate identity verification and data management approaches, organizations can build trust with their users, enhance security, and deliver seamless digital experiences in an increasingly interconnected world. The adoption of appropriate customer master data management and identity verification systems can shape the way customers interact with organizations for their joint success and confidence in dealing with one another in the years to come.